How Target Was Breached in 2013
In 2013, over 40 million credit card numbers were exfiltrated directly from the point-of-sale systems in more than 1800 Target stores. The attackers achieved this by deploying malware across multiple systems inside Target infrastructure. This is how they did it!
How It Happened
Initial Access
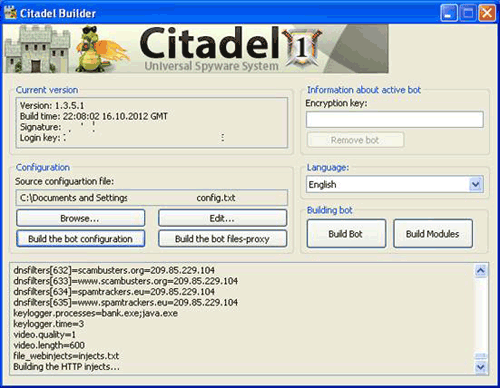
The incident began in September 2013 with a phishing email targeting Fazio Mechanical, a supplier of Target that specializes in refrigeration systems for supermarkets. The malicious email carried the Trojan virus called Citadel that was specially designed to steal passwords.
The attackers managed to obtain, with Citadel, the necessary credentials to access some web services exclusively available to Target’s suppliers. These services were primarily used for electronic billing and contract submission.
 The Partners Online Web application for target suppliers
The Partners Online Web application for target suppliers
Execution & Privilege Escalation
Target has never publicly disclosed the method through which the attackers exploited these web services. However, the leading theory suggests that suppliers might have been able to upload documents such as invoices via one of the web applications. The attacker could have exploited this functionality to upload a PHP file, which acted as a web shell, enabling them to execute commands directly on the system.
Once inside the network, the attackers had multiple paths they could take. According to Verizon, the security consultants hired by Target after the incident, a file containing multiple credentials was found on certain servers, some Apache Tomcat servers were still using default passwords, some MSSQL servers were using weak passwords, and several systems that were outdated and vulnerable.
Persistence & Lateral Movement
Regardless of the path chosen by the malicious actors, somewhere in November 2013 they succeeded in adding a new user to Target’s Active Directory. There was no network segmentation, and all the machines were easily accessible. As a result, this newly created user, named ttcopscli3acs\Best1_user, granted them access to any machine within Target’s infrastructure, including all the point-of-sale systems (cash register), in more than 1800 Target stores throughout the country.
For those who may not be familiar, Active Directory serves as a centralized repository for managing users and computers within a Windows-based ecosystem. From a hacker’s perspective, it’s often regarded as the ultimate target since it typically grants access to an entire company’s infrastructure once it is breached.
Collection
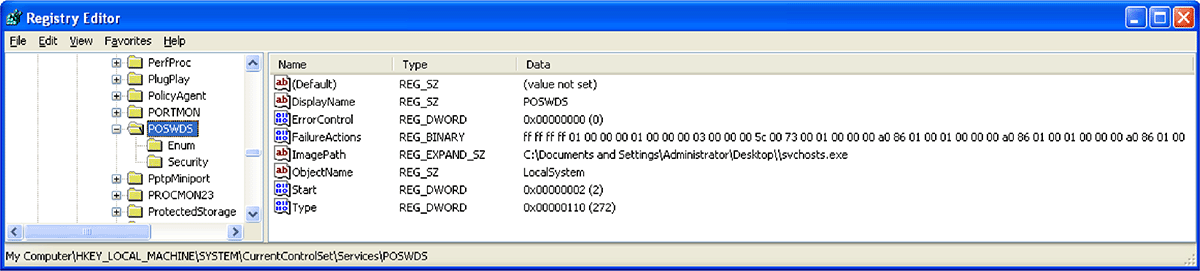
Once on the point-of-sale (POS) systems, the attackers deployed a modified version of BlackPos, a malware capable of scanning the memory of running processes with the goal of extracting credit card numbers as they were being processed during a transaction. The virus was installed as a Windows service named POSWDS and used the process name svchosts.exe masquerading as the legitimate Windows process svchost.exe.
The malware saved all the credit card numbers in the file winxml.dll located in C:\WINDOWS\system32. The file’s content was obfuscated using a non-standard base64 alphabet.
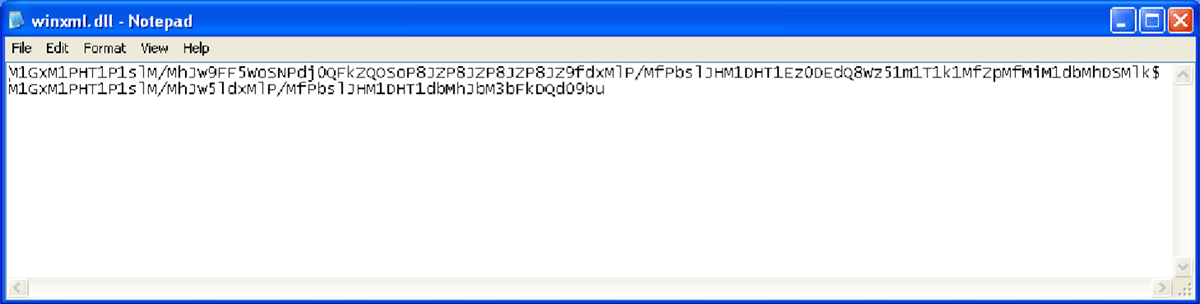 The obfuscated data in winxml.dll
The obfuscated data in winxml.dll
This particular type of malware was effective in 2013 because magnetic stripes transmit the credit card number as it was to the point of sale. However, today, the chip inside credit cards employs a cryptographic algorithm to protect the credit card number during transactions.
Exfiltration
Periodically, the malware launched an exfiltration routine to upload the file winxml.dll to a network location within Target’s network. The goal was to collect all the data from the various point-of-sale (POS) systems in a central location before exfiltration. In order to camouflage the data transfer, the routine was only executed during peak hours, which were between 10 a.m. and 5 p.m.
Here are the commands executed by the malware during this routine:
1
2
3
net use S: \\10.116.240.31\c$\WINDOWS\twain_32 /user:ttcopscli3acs\Best1_user BackupU$r
move C:\WINDOWS\system32\winxml.dll S:\%COMPUTERNAME%_28_11_10.txt
net use S: /del
Subsequently, a new malicious service named BladeLogic (once again mimicking the name of a legitimate service) took the files and uploaded them to multiple compromised FTP servers outside Target’s network. From these FTP servers, the malicious actor was able to simply download the exfiltrated files.
How It Was Detected
Target had no knowledge of the intrusion into their infrastructure. The malware on the point-of-sale had been detected multiple times by FireEye, their Endpoint Security system. However, their security analysts had concluded that these alerts were false positives.
It was the U.S. Department of Justice that initially detected a significant volume of suspicious activity involving credit cards used at Target stores and finally notified Target in December 2013, one month after the initial breach. In response, Target promptly initiated an investigation and quickly removed all malware from their infrastructure.
Conclusion
The attackers successfully exfiltrated 40 million credit card numbers through the malware deployed on the point-of-sale systems. Furthermore, they gained access to Target’s databases, allowing them to extract personal information from over 70 million customers.
I suspect that alert fatigue played a big role in this breach. When confronted with an overwhelming volume of alerts, many of which turn out to be false positives, security engineers often become desensitized and may overlook or disregard genuine alerts. This is likely why Target did not take action when their security system alerted them about the malware.
Sources
- A Kill Chain Analysis of the 2013 Target Data Breach | United States Senate
- Inside a Targeted Point-of-Sale Data Breach | Dell SecureWorks
- Retail Merchants Targeted by Memory-Parsing Malware | VISA
- New Clues in the Target Breach | Brian Krebs
- Inside Target Corp., Days After 2013 Breach | Brian Krebs
- Target POS Malware vs. Open Source Tools | BriMor Labs
- The Untold Story of the Target Attack Step by Step | Aorato Labs
Techniques
The MITRE ATT&CK techniques used by the attackers during their intrusion:
- Initial Access
- Execution
- Persistence
- Defense Evasion
- Collection
- Exfiltration