Hackfest 2022: Internet of Torments 2.0
Writeup for the “Internet of Torments 2.0” challenge created by @Miu. for the Hackfest CTF 2022.
01 - Flickering Light Bulb 💡 1/4
For this series of challenges, a Wireshark capture file BTLE_Capture.pcapng is provided.
The challenge name and file name indicate that we need to analyze Bluetooth packets from a smart light bulb.
If the packets are not decoded properly when opening the file in Wireshark, we can adjust this option:
Go to Preferences->Protocols->DLT_USER and enter “btle” as protocol
https://github.com/greatscottgadgets/ubertooth/issues/61
The first flag consists of finding the name of the light bulb:
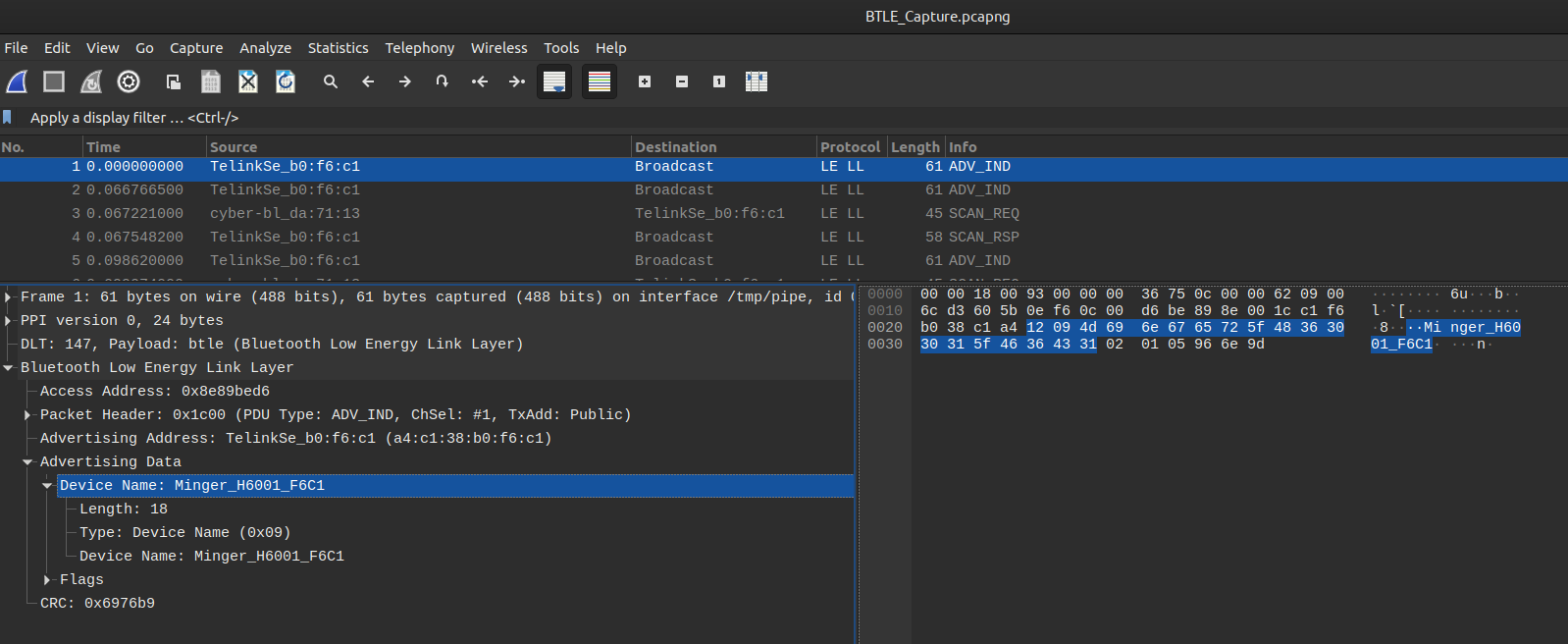
Simply take a packet of type ADV_IND to find the device name:
1
Minger_H6001_F6C1
02 - Flickering Light Bulb 💡 2/4
The second flag consists of finding the value that was sent to the bulb to change its color to blue.
By searching for the bulb’s model, we find this GitHub repository that explains how Bluetooth traffic works.
The handle used to send a request to the bulb is 0x15. To filter for these packets in Wireshark, we can use this filter.
1
btatt.handle == 0x15
Here’s an example of a value obtained in a packet:
1
33 05 02 ff7f00 00 ffc78f 000000000000000000 03
- Data type
0x33: RGB Data0xaa: ??
- Command type
0x01: Power0x04: Brightness0x05: Color
- Mode
0x02: Manual mode
- Color (
0xffffff) (if toggle is0x00) - Toggle
0x00: RGB0x01: Warm/Cold White
- Values for Warm/Cold White (if toggle à
0x01) - Zero padding
- Checksum
To find the flag, we need to find a packet with the color 0x0000ff. There are not many of them, so we can check them one by one and find this value:
1
3305020000ff00ffc78f0000000000000000007c
03 - Flickering Light Bulb 💡 3/4
The third flag consists of constructing the value to set the bulb to orange RGB(255, 87, 51).
Based on the documentation found earlier, we can construct the following value:
1
33 05 02 ff5733 00 000000 000000000000000000
We need to to recalculate the checksum, which should be af. https://www.scadacore.com/tools/programming-calculators/online-checksum-calculator
Here’s the final flag:
1
330502ff573300000000000000000000000000af
04 - Flickering Light Bulb 💡 4/4
The last flag consists of constructing the command to be sent once connected with gatttool to set the bulb to orange RGB(255, 87, 51).
The command follows the format char-write-req <handle> <new value>
The handle is the same as the one in the packet displayed in Wireshark.
So, here’s the flag:
1
char-write-req 0x0015 330502ff573300000000000000000000000000af

